NoScript Security Suite por Giorgio Maone
Disponible en Firefox para Android™Disponible en Firefox para Android™
The best security you can get in a web browser! Allow potentially malicious web content to run only from sites you trust. Protect yourself against XSS other web security exploits.
Necesitás Firefox para usar esta extensión
Metadata de la extensión
Capturas de pantalla
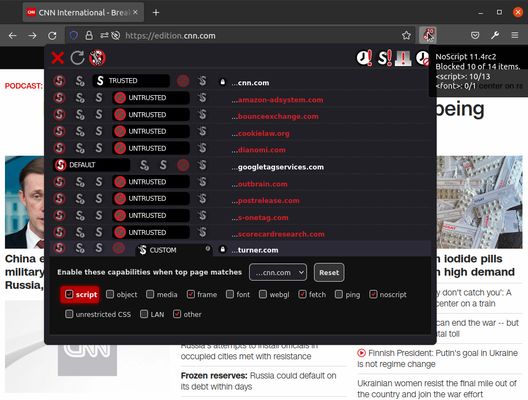
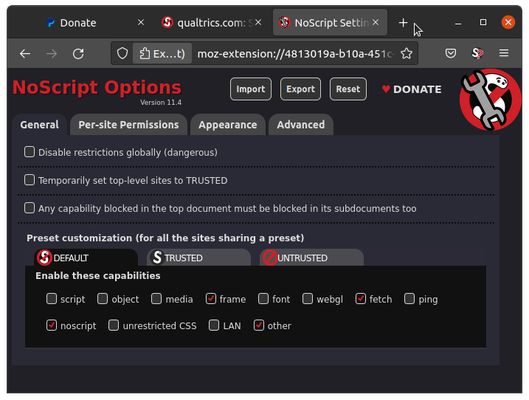
Sobre esta extensión
Winner of the "PC World - World Class Award" and bundled with the Tor Browser, NoScript gives you the best available protection on the web. It allows JavaScript, Flash, and other executable content to run only from trusted domains of your choice (e.g. your banking site), thus mitigating remotely exploitable vulnerabilities, such as Spectre and Meltdown.
It protects your "trust boundaries" against cross-site scripting attacks (XSS), cross-zone DNS rebinding / CSRF attacks (router hacking), and Clickjacking attempts, thanks to its unique ClearClick technology.
Such a preemptive approach prevents exploitation of security vulnerabilities (known and unknown!) with no loss of functionality where you need it.
Experts do agree: Firefox is really safer with NoScript!
FAQ: https://noscript.net/faq
Forum: https://noscript.net/forum
A Basic NoScript 10 Guide
Still confused by NoScript 10's new UI?
Check this user-contributed NoScript 10 primer.
and this NoScript 10 "Quantum" vs NoScript 5 "Classic" (or "Legacy") comparison.
It protects your "trust boundaries" against cross-site scripting attacks (XSS), cross-zone DNS rebinding / CSRF attacks (router hacking), and Clickjacking attempts, thanks to its unique ClearClick technology.
Such a preemptive approach prevents exploitation of security vulnerabilities (known and unknown!) with no loss of functionality where you need it.
Experts do agree: Firefox is really safer with NoScript!
FAQ: https://noscript.net/faq
Forum: https://noscript.net/forum
A Basic NoScript 10 Guide
Still confused by NoScript 10's new UI?
Check this user-contributed NoScript 10 primer.
and this NoScript 10 "Quantum" vs NoScript 5 "Classic" (or "Legacy") comparison.
Security issues affecting Firefox or the Tor Browser which can be fixed by a NoScript update are guaranteed to be addressed within 24 hours. This sometimes requires many updates to be issued in a short timespan, and when this happens you may notice NoScript UI's asking to "reload this page in order to operate properly". This is normal on "live" updates, and it just means the UI is out of sync with the page content, but there's no need to worry as all the restrictions to scripts and active content are still in place.
Calificá tu experiencia
Ayudar a este desarrollador
El desarrollador de esta extensión te pide lo ayudés a seguir con el desarrollo haciendo una pequeña contribución.
PermisosConocer más
Este complemento necesita:
- Acceder a las pestañas del navegador
- Acceder a actividad del navegador durante la navegación
- Acceder a tus datos para todos los sitios web
Más información
- Enlaces del complemento
- Versión
- 12.6
- Tamaño
- 963,61 KB
- Última actualización
- hace 9 días (28 de abr. de 2025)
- Categorías relacionadas
- Licencia
- Solo Licencia Pública General de GNU v2.0
- Política de privacidad
- Leer la política de privacidad de este complemento
- Historial de versiones
- Etiquetas
Agregar a la colección
Notas de prensa para 12.6
v 12.6
x Make contextual policies override restriction cascading
(tor-browser#43397)
x [Chromium] Fix 12.5.9xx prompt closure regression
x [Chromium] Full x-load checks Chromium support
x Better offscreen placeholders for x-load
x [l10n] [Chromium] Make x-load capability localization
Chromium-compatible
x [L10n] Updated de, fr, he, ru, tr zh_CN
x [UX] Honor non-contextual x-load capability granted from
NoScript Options (thanks barbaz for RFE)
x Prevent data: URIs from messing with srcset parsing
(thanks fatboy for reporting)
x Regard as "mutually safe" for x-load directories sharing a
common ancestor
x [UX] Make x-load capability visible for CUSTOM file:
entries in NoScript Options (thanks barbaz for RFE)
x [UX] Fixed prompt window leaks (tor-browser#43281)
x [UX] Make object unblocking temporary and contextual by
default, with choices in the prompt
x [nscl] Option to clone Permissions without context
x Always honor the "Collapse blocked objects" option
x Refactor top-level auto-trust and make it contextual
(issue #417)
x [nscl] Remove noisy debug statement
x [UX] UI support for extra floating capabilities (x-load)
x Integrate event handlers suppression with blocking if
needed (thanks Adithya Suresh Kumar for reporting)
x [nscl] Refactor xray proxification
x Fix incorrect assumptions about some DOM element
properties reflecting URLs (thanks Adithya Suresh Kumar
for reporting)
x [nscl] Fix race condition between multiple extensions
using MV3/DNR SyncMessage (JShelter#146, thanks polcak for
reporting)
x Suppress some event handlers (tor-browser#43491, thanks
Adithya Suresh Kumar for reporting)
x [build] Publish XPIs only after their signed
x [build] Improved version bump commit logic
x Make contextual policies override restriction cascading
(tor-browser#43397)
x [Chromium] Fix 12.5.9xx prompt closure regression
x [Chromium] Full x-load checks Chromium support
x Better offscreen placeholders for x-load
x [l10n] [Chromium] Make x-load capability localization
Chromium-compatible
x [L10n] Updated de, fr, he, ru, tr zh_CN
x [UX] Honor non-contextual x-load capability granted from
NoScript Options (thanks barbaz for RFE)
x Prevent data: URIs from messing with srcset parsing
(thanks fatboy for reporting)
x Regard as "mutually safe" for x-load directories sharing a
common ancestor
x [UX] Make x-load capability visible for CUSTOM file:
entries in NoScript Options (thanks barbaz for RFE)
x [UX] Fixed prompt window leaks (tor-browser#43281)
x [UX] Make object unblocking temporary and contextual by
default, with choices in the prompt
x [nscl] Option to clone Permissions without context
x Always honor the "Collapse blocked objects" option
x Refactor top-level auto-trust and make it contextual
(issue #417)
x [nscl] Remove noisy debug statement
x [UX] UI support for extra floating capabilities (x-load)
x Integrate event handlers suppression with blocking if
needed (thanks Adithya Suresh Kumar for reporting)
x [nscl] Refactor xray proxification
x Fix incorrect assumptions about some DOM element
properties reflecting URLs (thanks Adithya Suresh Kumar
for reporting)
x [nscl] Fix race condition between multiple extensions
using MV3/DNR SyncMessage (JShelter#146, thanks polcak for
reporting)
x Suppress some event handlers (tor-browser#43491, thanks
Adithya Suresh Kumar for reporting)
x [build] Publish XPIs only after their signed
x [build] Improved version bump commit logic
Más extensiones de Giorgio Maone
- Todavía no hay valoraciones
- Todavía no hay valoraciones
- Todavía no hay valoraciones
- Todavía no hay valoraciones
- Todavía no hay valoraciones
- Todavía no hay valoraciones